This post was originally published on Security Affairs. It can be found here.
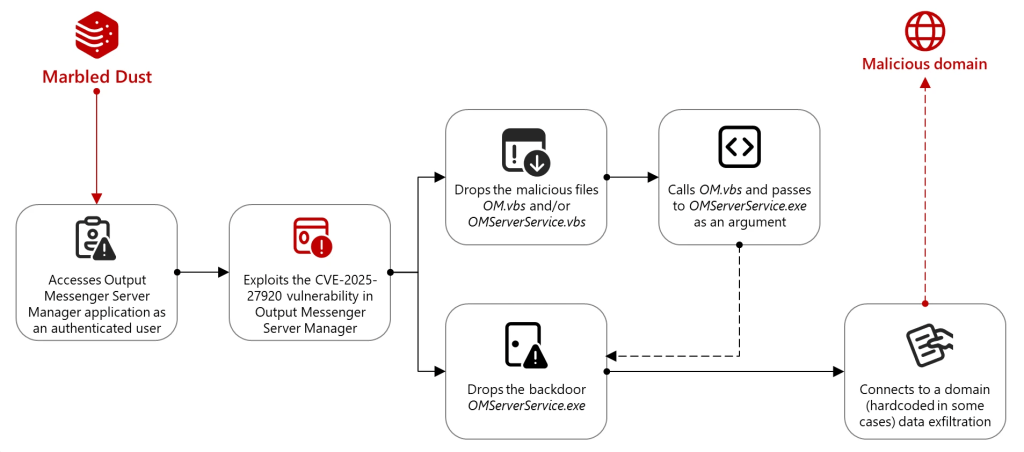
Expert found two flaws in DriverHub, pre-installed on Asus motherboards, which allow remote code execution via crafted HTTP requests.
Security researcher ‘MrBruh’ discovered two vulnerabilities, tracked as CVE-2025-3462 (CVSS score of 8.4) and CVE-2025-3463 (CVSS score of 9.4), in DriverHub, a driver that is pre-installed on Asus motherboards. A remote attacker can exploit the flaws to gain arbitrary code execution.
Both flaws stem from insufficient validation, allowing misuse of DriverHub features. The company pointed out that the flaws don’t impact laptops and desktops.
DriverHub, a driver updater with no GUI, runs a background process that talks to driverhub.asus.com via RPC on localhost port 53000. Researcher MrBruh found that while it only accepts requests with an origin header set to “driverhub.asus.com,” a flawed wildcard match allowed requests from domains like “driverhub.asus.com.mrbruh.com.” An attacker can exploit this vulnerability to install malicious software.
Researcher MrBruh discovered that Asus DriverHub exposes several local RPC endpoints, including dangerous ones like UpdateApp, which downloads and installs executables with admin rights if signed by Asus. By analyzing JavaScript and decompiled code, he found that a zip file used in driver installs includes an INI setting (SilentInstallRun) that can execute arbitrary commands during silent installs. This opens a path to remote code execution (RCE).
“The files of importance here are the AsusSetup.exe, AsusSetup.ini and SilentInstall.cmd. When executing AsusSetup.exe it first reads from AsusSetup.ini, which contains metadata about the driver. I took interest in a property in the file: SilentInstallRun.” reads the report published by MrBrush. “When you double-click AsusSetup.exe it launches a simple gui installer thingy. But if you run AsusSetup.exe with the -s flag (DriverHub calls it using this to do a silent install), it will execute whatever’s specified in SilentInstallRun. In this case the ini file specifies a cmd script that performs an automated headless install of the driver, but it could run anything.”
The exploit chain abuses Asus DriverHub’s update mechanism: a malicious site on a spoofed subdomain sends requests to download a benign-sounding executable and a crafted AsusSetup.ini. Then, it downloads a legitimate, signed AsusSetup.exe, which runs silently with admin rights and executes the attacker’s payload (calc.exe) as specified in the .ini file.
MrBruh discovered the flaw on April 7 and reported the vulnerabilities on April 8. Asus released security updates on May 9.
MrBruh asked Asus if they offered bug bounties. The company said they don’t offer bug bounties but would add the researcher’s name to their “hall of fame.”
“I asked ASUS if they offered bug bounties. They responded saying they do not, but they would instead put my name in their “hall of fame”. This is understandable since ASUS is just a small startup and likely does not have the capital to pay a bounty.” concludes MrBruh.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
Pierluigi Paganini
(SecurityAffairs – hacking, ASUS)
This post was originally published on this site